
Our strategic, risk-focused approach spans collaboration, identity, endpoint, and data environments, empowering you to take control of your cybersecurity landscape. This engagement identifies threat detection and mitigation through targeted insights and immediate recommendations, while also developing a Zero Trust-aligned cybersecurity roadmap. The outcome is a prioritized, actionable plan designed to reduce exposure, improve security control effectiveness, and fortify your long-term security posture against evolving threats.

Entra ID (AAD) Identity Protection

Microsoft Defender Office & Cloud Apps

Microsoft Defender for Identity & Endpoint

Microsoft Sentinel

Microsoft Security Copilot
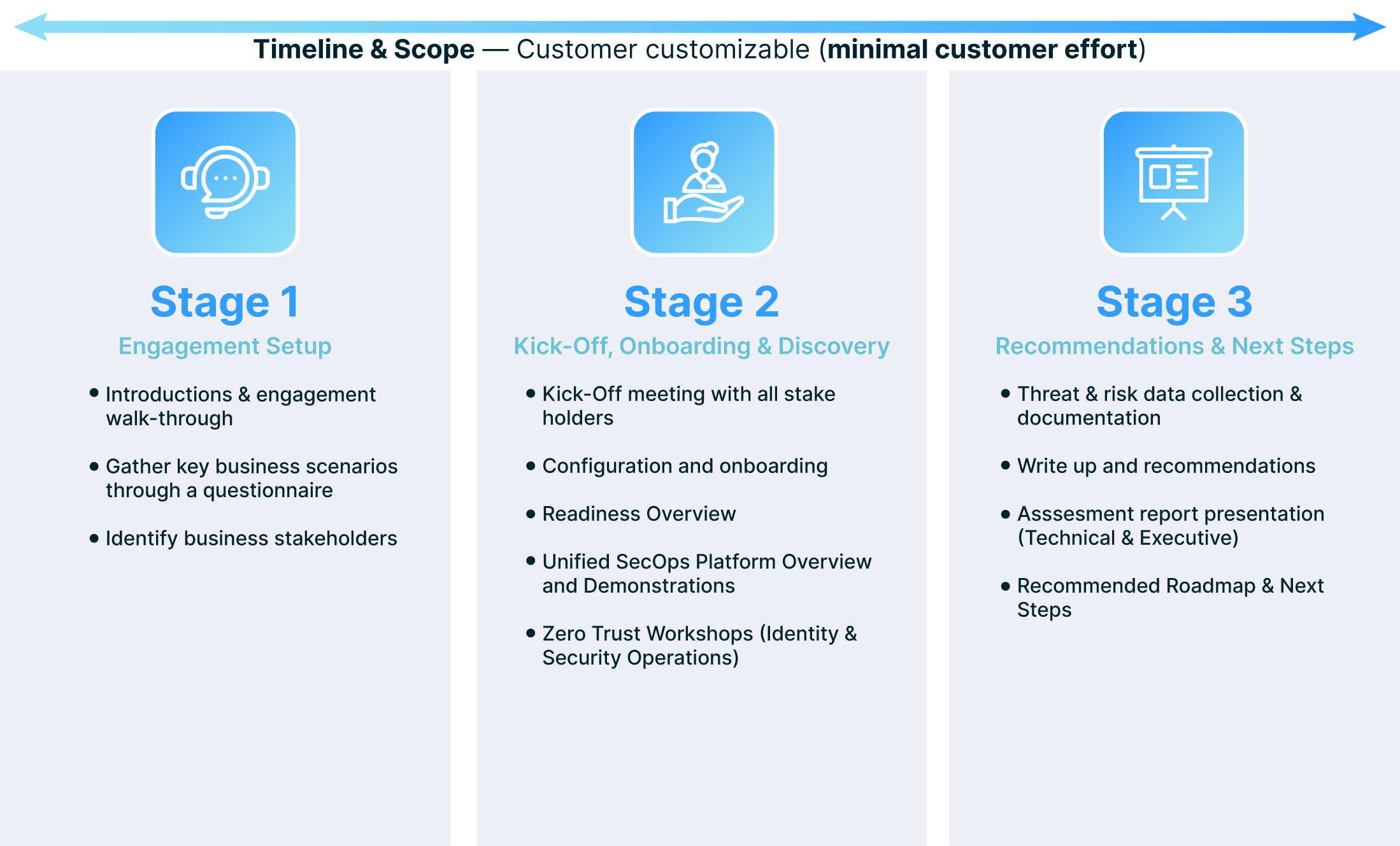

Designed to help you protect your organization from cyber threats and vulnerabilities. It is a three-day (over three-weeks) engagement that uses specialized tools and methods to scan your environment and identify risks or gaps in your security posture. The assessment will also provide you with clear recommendations and best practices on how to improve your security and reduce your exposure to cyberattacks.

Reduce risk by finding and removing implicit assumptions of trust. We conduct guided workshops in which our delivery experts will work with you to discuss your current state, provide education on recommended best practices, and help you to develop an actionable roadmap for implementing a secure Zero Trust posture.

Download files that explain the offer in deeper detail:


